- 1) How can we reset the SIM Module? …
- 2) What do you understand by High Availability? …
- 3) What are the types of user authentication? …
- 4) How are users authenticated? …
- 5) What is the process of setting the HA Host Offline?
IBM QRadar Interview Questions and Answers | SOC SIEM SOAR UEBA | Cybersecurity | SOC Analyst
We help you to choose the right Python career Path at myTectra. Here are the top courses in Python one can select. Learn More →
Learn Advanced IBM Security QRadar SIEM Certification Training Course to Build Your Skills
34. What is NetFlow?
Ans:
It is s proprietary accounting technology designed by Cisco, which monitors traffics through routers, & interprets the client, protocol, server & port used, calculates the number of bytes & packets to send the data to any NetFlow collector. The procedure of sending data from NetFlow is known as a NetFlow Data Export (NDE).
35. What are the databases present in IBM QRadar SIEM?
Ans:
QRadar has 3 databases. They contain data and configuration information. Configuration information can additionally be found in txt.files.
36. How the encryption process is enabled?
Ans:
Answer: IBM QRadar provides encryption support that uses OpenSSH to provide secure data transmission between the devices connected in your network. At least one managed host is required to enable the encryption process because encryption occurs between managed hosts only. After the enabling of the encryption process, a secure tunnel is created on the client that initiates the connection using an SSH protocol.
37.What is the simple meaning of QRadar architecture
Ans:
The QRadar architecture functions the same way regardless of the size or number of components in a deployment. The following three layers that are represented in the diagram represent the core functionality of any QRadar system.
38.What is Data collection
Ans:
Data collection is the first layer, where data such as events or flows is collected from your network. The All-in-One appliance can be used to collect the data directly from your network or you can use collectors such as QRadar Event Collectors or QRadar QFlow Collectors to collect event or flow data. The data is parsed and normalized before it passed to the processing layer. When the raw data is parsed, it is normalized to present it in a structured and usable format.The core functionality of QRadar SIEM is focused on event data collection, and flow collection.Event data represents events that occur at a point in time in the user’s environment such as user logins, email, VPN connections, firewall denys, proxy connections, and any other events that you might want to log in your device logs.Flow data is network activity information or session information between two hosts on a network, which QRadar translates in to flow records. QRadar translates or normalizes raw data in to IP addresses, ports, byte and packet counts, and other information into flow records, which effectively represents a session between two hosts. In addition to collecting flow information with a Flow Collector, full packet capture is available with the QRadar Incident Forensics component.
39.What is Data processing
Ans:
After data collection, the second layer or data processing layer is where event data and flow data are run through the Custom Rules Engine (CRE), which generates offenses and alerts, and then the data is written to storage.Event data, and flow data can be processed by an All-in-One appliance without the need for adding Event Processors or Flow Processors. If the processing capacity of the All-in-One appliance is exceeded, then you might need to add Event Processors, Flow Processors or any other processing appliance to handle the additional requirements. You might also need more storage capacity, which can be handled by adding Data Nodes.Other features such as QRadar Risk Manager (QRM), QRadar Vulnerability Manager (QVM), or QRadar Incident Forensics collect different types of data and provide more functions.QRadar Risk Manager collects network infrastructure configuration, and provides a map of your network topology. You can use the data to manage risk by simulating various network scenarios through altering configurations and implementing rules in your network.Use QRadar Vulnerability Manager to scan your network and process the vulnerability data or manage the vulnerability data that is collected from other scanners such as Nessus, and Rapid7. The vulnerability data that is collected is used to identify various security risks in your network.Use QRadar Incident Forensics to perform in-depth forensic investigations, and replay full network sessions.
40.What do you know about the Data searches
Ans:
In the third or top layer, data that is collected and processed by QRadar is available to users for searches, analysis, reporting, and alerts or offense investigation. Users can search, and manage the security admin tasks for their network from the user interface on the QRadar Console.In an All-in-One system, all data is collected, processed, and stored on the All-in-One appliance.In distributed environments, the QRadar Console does not perform event and flow processing, or storage. Instead, the QRadar Console is used primarily as the user interface where users can use it for searches, reports, alerts, and investigations.
41.What does a SIEM tool do?
Ans:
SIEM software combines security information management (SIM) and security event management (SEM) to provide real-time analysis of security alerts generated by applications and network hardware
42.How QRadar SIEM can help your business?
Ans:
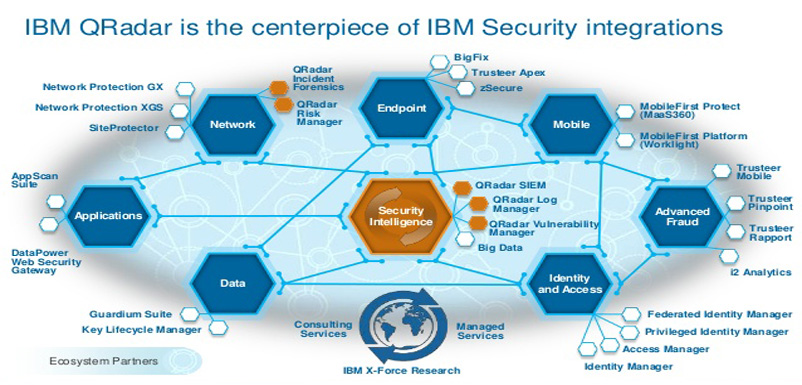
43.What is the function of index management toolbar?
Ans:
Index management is used to control the indexing of the database on event and flow properties.
44.Is SIEM a Darktrace?
Ans:
Darktrace can be configured to fit into SIEM dashboards, so alerts from threats detected by the Darktrace Cyber AI Platform can be sent to security teams via the SIEM. SIEMs can be a useful tool for data correlation and the convergence of security tools.
45.What is SOC and NOC?
Ans:
A Network Operations Center (NOC) maintains optimal network performance, while a Security Operations Center (SOC) identifies, investigates, and resolves threats and cyber attacks.
46.What should a SOC analyst know?
Ans:
Top 5 skills a SOC analyst needs
47.Who invented SIEM?
Ans:
The term SIEM was coined in 2005 by Mark Nicolett and Amrit Williams, in Gartner’s SIEM report, Improve IT Security with Vulnerability Management. They proposed a new security information system, on the basis of two previous generations.
48.Is SIEM a monitoring tool?
Ans:
SIEM works by combining two technologies:
49.Why do we need SIEM?
Ans:
SIEM is important because it makes it easier for enterprises to manage security by filtering massive amounts of security data and prioritizing the security alerts the software generates. SIEM software enables organizations to detect incidents that may otherwise go undetected.
50.How does QRadar Siem work?
Ans:
The core functionality of QRadar SIEM is focused on event data collection, and flow collection. … QRadar translates or normalizes raw data in to IP addresses, ports, byte and packet counts, and other information into flow records, which effectively represents a session between two hosts.
51.What is Q radar?
Ans:
IBM QRadar is an enterprise security information and event management (SIEM) product. It collects log data from an enterprise, its network devices, host assets and operating systems, applications, vulnerabilities, and user activities and behaviors.
52.When was the first SIEM?
Ans:
SIEM 1.0 circa 2006 – A revolutionary new approach to security. The arrival of the first generation of SIEM platforms heralded a new dawn in the data security industry, combining security event management with security information management for the first time.
53.What is Q radar?
Ans:
IBM QRadar is an enterprise security information and event management (SIEM) product. It collects log data from an enterprise, its network devices, host assets and operating systems, applications, vulnerabilities, and user activities and behaviors.
54.What database does QRadar use?
Ans:
Postgres is used for configurations and functionality related to QRadar. Ariel is a custom minute-by-minute event database created by the QRadar dev team to capture and write events to disk in /store/ariel.
55.What is QRadar event collector?
Ans:
QRadar Event Collector. The Event Collector collects events from local and remote log sources, and normalizes raw log source events to format them for use by QRadar. The Event Collector bundles or coalesces identical events to conserve system usage and sends the data to the Event Processor.
56.What is IBM security QRadar?
Ans:
IBM® QRadar® Security Information and Event Management (SIEM) helps security teams accurately detect and prioritize threats across the enterprise, and it provides intelligent insights that enable teams to respond quickly to reduce the impact of incidents. … QRadar SIEM is available on premises and in a cloud environment
57.How QRadar Siem collects security data?
Ans:
IBM QRadar collects log data from sources in an enterprise’s information system, including network devices, operating systems, applications and user activities. The QRadar SIEM analyzes log data in real-time, enabling users to quickly identify and stop attacks.
58.What is the basic value proposition of IBM security QRadar?
Ans:
It automatically analyzes and aggregates log and flow data from thousands of devices, endpoints and apps across your network, providing single alerts to speed incident analysis and remediation.
59.What does SOC mean in security?
Ans:
Security Operation CenterShare: A Security Operation Center (SOC) is a centralized function within an organization employing people, processes, and technology to continuously monitor and improve an organization’s security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents.
60.What is IBM verify?
Ans:
What is IBM Verify? IBM Verify adds an extra layer of security to your online services. Two-step verification helps protect your accounts from the bad guys, even if they steal your password. Why you need IBM Verify. Passwords are no longer secure enough to protect your information on their own.
61. What is Implementation Flow-Chart?
Ans:
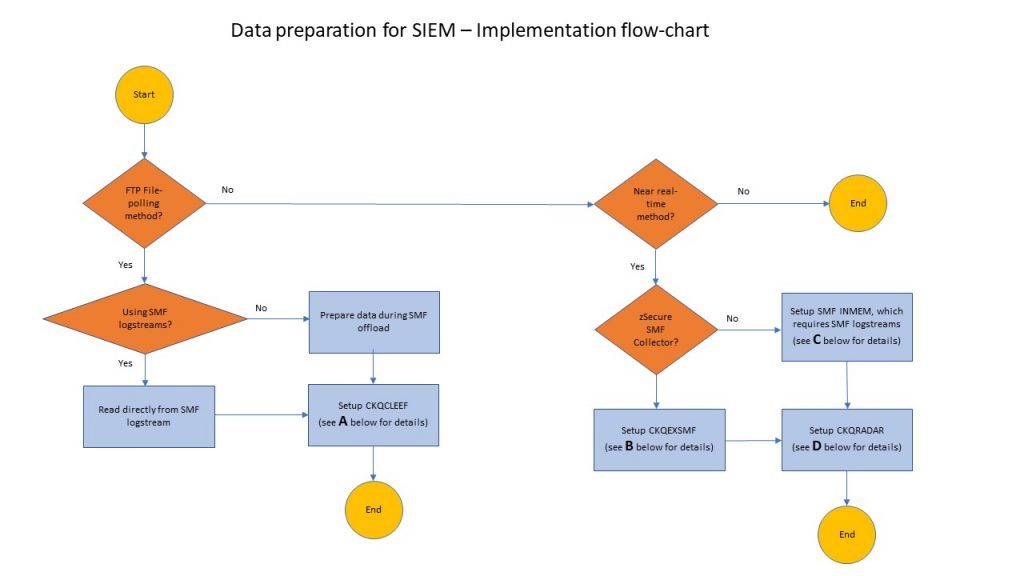
62. How to manage the sequence of the retention bucket?
Ans:
Retention buckets are sequenced in order from top to bottom row. The order of the retention bucket can be changed as required. The data is stored in the retention bucket if it matches the criteria of that bucket. The sequence of retention bucket can be changed in the following order:

Share this:
The main components of a QRadar SIEM deployment are the Console, the Event Processor, and the Data Node. The Console is the web-based interface used to manage and configure the system, while the Event Processor is responsible for collecting, processing, and storing data. The Data Node is used to store long-term data and can be used for reporting and analysis.
Network hierarchy mapping is a process of creating a map of the relationships between different network elements, in order to better understand how they interact with each other. This is similar to network topology, but network hierarchy mapping goes a step further by also taking into account the different levels of abstraction that exist within a network. This can be helpful in understanding how different parts of a network fit together, and in identifying potential areas of improvement.
The best way to check if a host or device is sending data to QRadar properly is to use the “Live Data” feature in the QRadar console. This will allow you to see in real-time the data that is being sent to QRadar from the host or device in question. If you do not see any data coming in, then there may be an issue with the configuration of the host or device.
QRadar is a security platform that helps organizations detect and respond to threats in real time. As a result, it is an increasingly popular tool for security professionals. When interviewing for a position that uses QRadar, it is important to be prepared to answer questions about your experience and knowledge of the platform. In this article, we review some of the most common QRadar interview questions and provide tips on how to answer them.
QRadar uses a role-based access control model to control user authentication and authorization. This means that there are a set of predefined roles that users can be assigned to, and each role has a set of permissions associated with it. When a user tries to access a QRadar feature, the system checks to see if the user has the appropriate permissions for that feature. If the user does not have the necessary permissions, they will not be able to access the feature.
FAQ
Is IBM QRadar a SIEM?
What is IBM QRadar network security?
What is IBM QRadar used for?
What database does IBM QRadar use?
